Aside from your Windows Hello biometrics, your Windows PIN and your Microsoft account, your Windows password forms the first layer of security provided by Microsoft to all Windows users. But where is your password actually stored? How do you access it? And can you recover it in case you ever forget it? These are the basic things we will be looking at in this article, so that by the end of it you will have a fair understanding of how the windows password system works. Although this is similar to how things work in other operating systems, Windows has been around for a long time, so their system has a lot of legacy elements that could make it sound more complex than it actually is.
Where is Your Windows Username and Password Stored? How to Find It
The Windows password is usually "hashed" and stored in the Windows SAM file or security account manager file. The file is located on your system at this particular file path: C:\Windows\System32\Config.
However, on normal boot up of your operating system, this file is not accessible. The hash values are also stored in a different location, which is your registry. This will be stored in the following location: HKEY_ LOCAL_MACHINE\SAM.
Again, this particular location cannot be accessed when the OS is booted up.
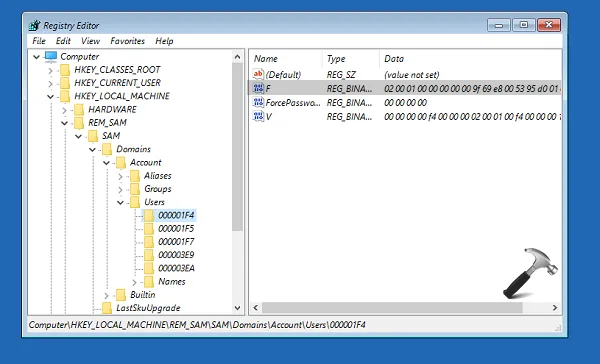
How Do I Access My Username and Password?
There are several methods and tools to accomplish this, including physical access to the SAM file. One of the easiest ways, especially if you have physical access to your hard drive, is to use a different operating system to boot your computer. One way to do this is by using a Linux live CD which can read NTFS drives. Once you mount the Windows partition, you can simply copy the SAM file to external media such as a USB drive or a writable DVD or CD.
But before you access your SAM files and the password hashes contained in those files, you need to understand a little bit about what password hashing means.

Password Hashing
Password hashing is essentially a one-way method to transform your password so that it becomes unreadable to anyone. It is almost impossible to reverse-engineer a password hash because of the one-way conversion process.
The hashing algorithms use complex mathematical formulae to create the hashes, which is why it is so difficult or nearly impossible to work out the passwords based on the hashes.

For this reason, security researchers have developed several other means of recovering a password, as we will describe below. The fact that the locations where these hashed passwords are stored are not easily accessible when the operating system itself boots up forms a strong layer of security when someone tries to compromise your machine. Of course, that does not mean that a password can never be recovered; it only means that specialised tools and a little bit of technical expertise is required to do so.
Other ways to access Hashed Passwords
There are several programs that have been created that can extract the password hashes from your SAM file and either recover or reset the password. The majority of these tools use one or more techniques, like the password reset disk method, for example. This is probably one of the easiest ways to extract hashed passwords and reset or recover them, and there are several freeware as well as premium utilities developed specifically for this purpose.
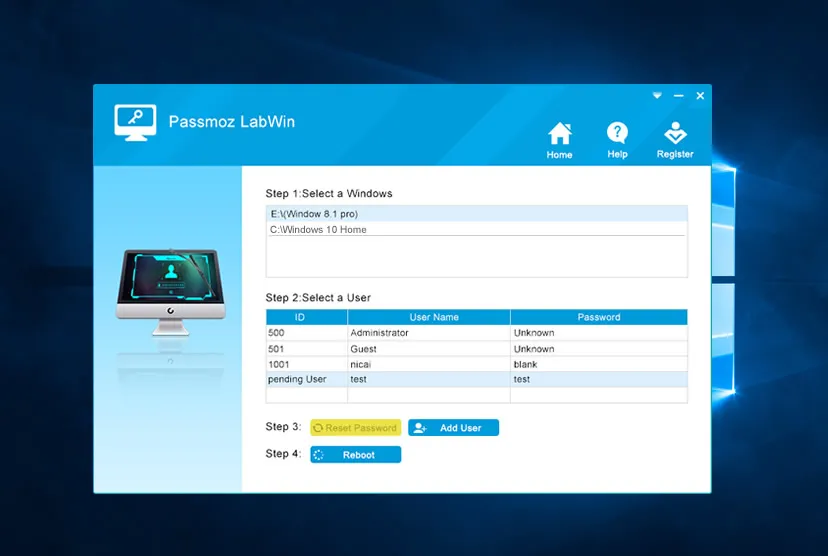
Can My Password Be Recovered from These Hashes?
Yes, although it is not easy to recover a password that has been forgotten or lost, it is not impossible. As mentioned, there are several tools to help you do this.
But before we look at any specific password recovery tools, let's explore how passwords are actually recovered. A lot of Windows users simply assume that if they have forgotten their passwords, then they need to reinstall their Windows operating system completely. This is a fallacy because password recovery methods do not require a complete OS installation.
One of the most popular methods of password recovery is to create a password reset disk. If you still have access to your Windows account, then you can create this disk under the assumption that you may forget your password in future. Then, when you actually do forget your password or lose it, you can use this password reset disk to quickly and easily reset your password and enter your PC without a problem.
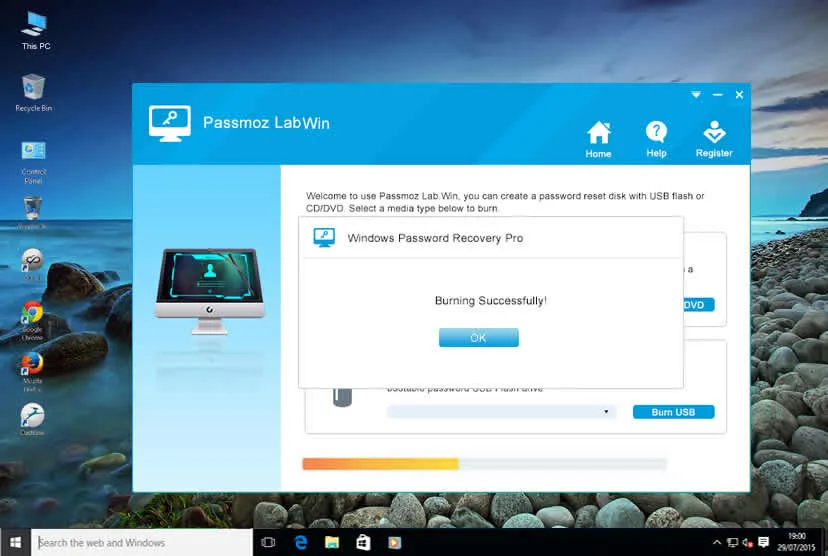
The next scenario is to crack a password that has already been forgotten, but a password reset disk was never created in the first place. In this instance, you will either need to create a password reset disk on a different PC or on a different installation of Windows on the same PC. What these tools do is to either recover, reset or erase your password so that getting in is made possible. Some of them have certain limitations, such as the maximum length or complexity of the password, whether or not you have access to a different user account on the same PC, and so on.
In general, a good password recovery utility will never mess around with the data in your system. The most it will do is manipulate your Windows registry in such a way that the password is either cracked or completely removed. So, if you see a review about a password recovery software where some users are seeing their data either go missing or being corrupted in some way, it is advisable to stay away from that particular piece of software. Fortunately, there are literally dozens of other choices to pick from.
Another consideration is the complexity of the password recovery method from the users perspective. Some of them require an extensive amount of command line work. Others may require additional software, such as utilities to burn ISO files to a drive or a disk. Yet others may require a dozen or more steps to recover the password, and they will often need the user to have some sort of technical acuity.
Final Words
In the end, the choice is yours. You can either go with a well known and widely used software application that requires very little user input, or you can go with one of the many open source utilities available for password recovery.
For example, PassMoz LabWin is a great tool for quick and easy password recovery. There are also open source tools like Ophcrack, John the Ripper, Mimikatz, Hashcat and others. As mentioned, only a few of them like PassMoz require very little user input. Most require some level of technical knowledge. However, the majority of them that are popular around the world are there for a reason - they work!





